Governance & Risk Model
Overview
The CRF’s Governance and Risk Model provides organizations with a robust framework for managing cybersecurity risks effectively. It emphasizes a structured approach to identifying, analyzing, and mitigating risks, ensuring that cybersecurity measures align with organizational strategies and business goals.
Benefits
- Strategic Risk Management: Enhances the ability to manage risks strategically by identifying and prioritizing potential threats and vulnerabilities.
- Compliance and Resilience: Aids in achieving compliance with legal and regulatory requirements while enhancing the organization’s resilience against cyber threats.
- Enhanced Decision Making: Empowers leaders with critical insights to make informed decisions about cybersecurity investments and strategies.
The GRM Management Lifecycle
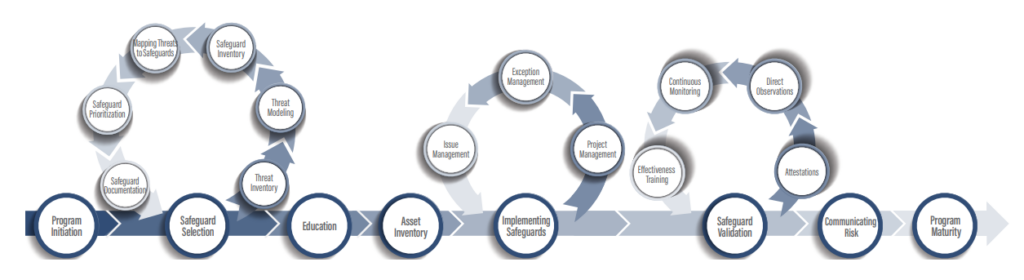
In the CRF-GRM, we discuss how the cybersecurity risk management lifecycle broadly divides into multiple phases: safeguard selection, asset inventory, and safeguard validation. Organizations must delve deeper into these phases to gain a more comprehensive understanding, identifying and addressing the specific steps involved. Each phase encompasses multiple stages, which organizations should approach sequentially. The outcomes of the initial stages serve as valuable inputs for the subsequent ones.
Throughout each step of these phases, the information gathered plays a crucial role in informing decisions in later stages. By methodically collecting and analyzing data at every point, organizations can make more informed, strategic decisions that enhance their overall cybersecurity posture. This approach ensures a dynamic and responsive risk management lifecycle, continually adapting to new information and evolving threats.
The subsequent diagram presents a detailed overview of the stages involved in the risk management lifecycle. We will delve into each stage to provide a more comprehensive understanding. After an organization completes its first iteration through this lifecycle, it may revisit and modify the data from any stage. However, any alterations must be followed by a thorough re-assessment of the subsequent stages, integrating the newly revised data. This process ensures a robust and continuous refinement of the risk management strategy. It allows the organization to adapt its approach based on the latest insights and maintain a proactive stance in its cybersecurity efforts.
Intended Audience
- Risk Managers: Who need to understand and mitigate potential cybersecurity risks.
- Cybersecurity Professionals: Looking to enhance their strategies with a structured risk management approach.
- Business Executives: Who must integrate cybersecurity risk management with business operations.
A Cycle of Continuous Improvement
Adopting the CRF’s Governance and Risk Model will fortify your organization’s defense mechanisms against evolving cybersecurity threats. Implementing the GRM model can improve your risk management processes and enhance organizational security.
Frequently Asked Questions
The Governance and Risk Model is a comprehensive framework designed to guide organizations through the process of identifying, assessing, and mitigating cybersecurity risks. It emphasizes the importance of aligning cybersecurity initiatives with business objectives, ensuring a proactive approach to digital threats, and fostering a culture of continuous improvement.
In today's digital landscape, cyber threats are evolving rapidly, posing significant risks to organizations of all sizes. The Governance and Risk Model provides a structured approach to cybersecurity, helping organizations not only protect their digital assets but also ensure that their cybersecurity efforts support overall business growth and success. It's crucial for maintaining compliance, building stakeholder trust, and ensuring business continuity.
The model starts with program initiation, defining the scope, objectives, and governance structure of your cybersecurity efforts. It then moves through strategic safeguard selection, workforce education, asset inventory and prioritization, and the implementation and validation of cybersecurity measures. The cycle of continuous improvement ensures that your cybersecurity posture evolves in line with new threats and organizational changes.
Successful implementation of the model requires involvement across the organization. This includes senior leadership to provide strategic direction and resources, IT and cybersecurity professionals to manage technical aspects, and employees at all levels to adhere to cybersecurity policies and procedures. Additionally, a dedicated Cybersecurity Steering Committee can oversee and guide the program's implementation.
Begin by downloading the free PDF version of the Governance and Risk Model to understand its framework and principles. Next, establish a Cybersecurity Steering Committee to lead the initiative, and develop a cybersecurity program charter that outlines your strategy, objectives, and governance structure. From there, follow the model's steps to assess risks, select and implement safeguards, educate your workforce, and continuously monitor and improve your cybersecurity posture.