Threat Taxonomy
What Is the CRF Threat Taxonomy?
The CRF – Threat Taxonomy (CRF–TT) is one of the most comprehensive frameworks available for identifying and categorizing cybersecurity threats. While many organizations rely on narrow threat feeds or high-level threat groupings, few have attempted to define a full-spectrum threat model designed specifically to support governance and safeguard selection. The CRF–TT fills that gap.
By organizing threats into well-defined categories and subcategories—each with clear criteria and rating factors—the taxonomy helps organizations understand which threats are most relevant to their environment and how to prioritize safeguards accordingly. It’s not just a list of possible attacks—it’s a strategic tool for aligning cybersecurity investments with real-world risk.
Why You Need a Structured Threat Taxonomy
Selecting and prioritizing cybersecurity safeguards requires a clear understanding of the threats they are intended to mitigate. Yet in many organizations, this foundational step is often approached in an ad hoc or inconsistent manner—leading to redundant analyses, incomplete coverage, and misaligned investments. The CRF–Threat Taxonomy (CRF–TT) addresses this challenge by providing a standardized, comprehensive taxonomy of threats that can be used across teams and disciplines.
Rather than developing a threat model from scratch, organizations can adopt the CRF–TT as a ready-made framework for mapping threats to safeguards, assessing relative risk, and justifying implementation priorities. It brings structure and clarity to the often ambiguous process of risk identification, enabling teams to move beyond intuition or generic lists and toward data-driven, strategically aligned security decisions.
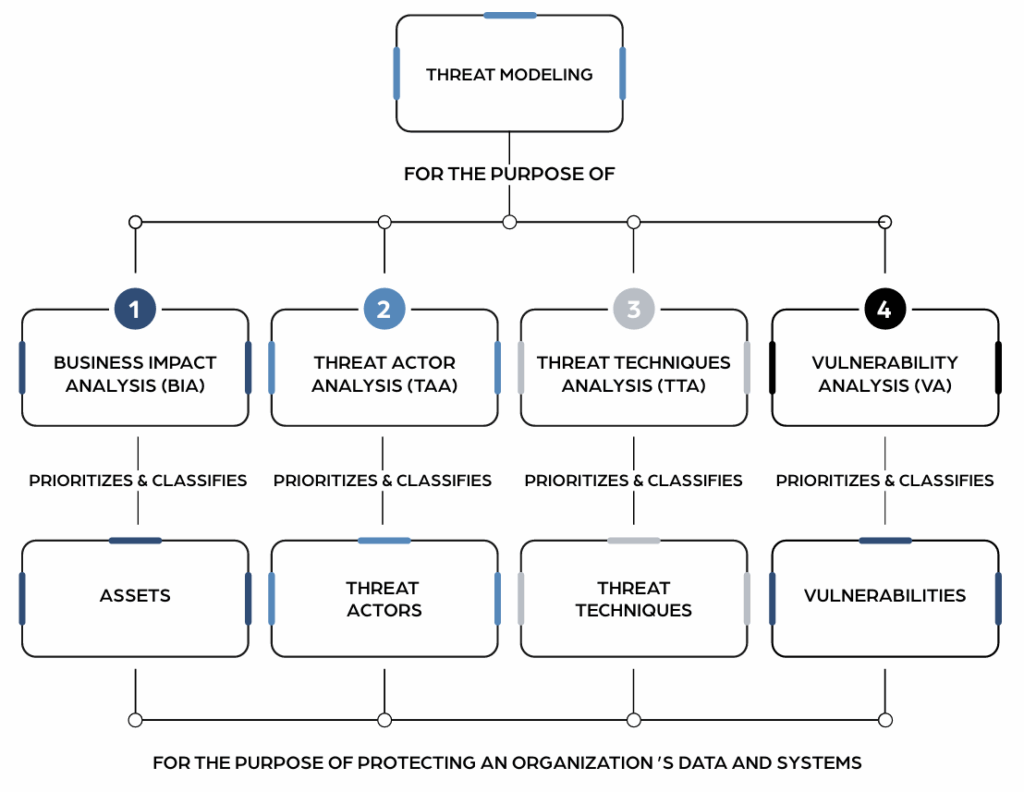
What You’ll Get
The 2025 edition of the CRF-TT includes an expanded set of threat definitions and a new threat rating system that evaluates severity, likelihood, and business impact. Each threat is assessed across multiple dimensions such as attacker capability, ease of exploitation, and potential harm to confidentiality, integrity, and availability. The taxonomy is also mapped to widely used threat models in the industry, ensuring compatibility and strategic alignment.
Key Takeaways
- Organized framework for classifying and prioritizing threats
- Multi-dimensional threat rating system for deeper analysis
- Compatible with leading industry threat models
- Supports both technical and executive-level decision-making
- Built for governance, not just reactive intel
Who Is This For?
This resource is designed for:
- Cybersecurity program leaders building threat-informed strategies
- Governance and risk professionals needing a threat model reference
- Security teams prioritizing safeguards based on actual risk
- Business leaders who want to understand threats in practical terms
Whether you’re running tabletop exercises, refining risk assessments, or aligning teams under one threat model—CRF-TT helps you do it smarter.
What’s New in v2025?
- Threat Rating System: Evaluate threats by likelihood, impact, and exploitability
- Expanded Definitions: More detailed and granular threat categorizations
- Model Alignment: Mapped to leading threat models for industry consistency
- Better Prioritization Tools: Enables safeguard alignment based on threat severity and relevance
Frequently Asked Questions
The CRF's Threat Taxonomy is a comprehensive framework designed to classify and categorize cybersecurity threats. It breaks down threats into manageable categories based on their characteristics, such as origin, attack methods, and potential impacts, facilitating a deeper understanding and more effective management of cybersecurity risks.
Utilizing The CRF's Threat Taxonomy enables your organization to prioritize cybersecurity efforts effectively, focusing on the most significant risks. It enhances strategic planning, improves response capabilities, and ensures compliance with regulatory standards by providing a clear, structured approach to threat analysis.
The development and upkeep of The CRF's Threat Taxonomy should be a collaborative effort, involving cybersecurity experts, IT personnel, and key stakeholders across your organization. Incorporating diverse perspectives ensures a thorough understanding of potential threats and enhances the taxonomy's relevance and effectiveness.
Yes, The CRF's Threat Taxonomy is designed to complement and enhance existing cybersecurity frameworks within your organization. Its flexible structure allows it to be seamlessly integrated with widely recognized frameworks such as ISO 27001, NIST Cybersecurity Framework, or CIS Controls. By aligning The CRF's Threat Taxonomy with these frameworks, organizations can ensure a comprehensive approach to cybersecurity that covers all aspects of threat identification, assessment, and mitigation, enhancing overall security posture and strategic risk management.
The CRF's Threat Taxonomy is instrumental in helping organizations systematically understand and categorize cybersecurity risks. By providing a structured framework for classifying threats based on their characteristics, such as origin, method of attack, and potential impact, it enables organizations to gain a comprehensive view of the cybersecurity landscape. This detailed understanding is crucial for developing targeted strategies for threat mitigation and prioritizing cybersecurity efforts. While the direct application to incident response wasn't explicitly detailed in the shared content, the foundational understanding and categorization of threats are essential steps in preparing for and responding to cyber incidents effectively.