Business Intelligence Model
Overview
The CRF-Business Intelligence Model (CRF-BIM) offers a structured, seven-step approach to transform manual cybersecurity assessments into automated, data-driven validation processes. By aligning safeguards with technical tools, integrating vendor data, and centralizing reporting, the model enables organizations to reduce risk exposure, improve visibility, and support smarter decision-making across all levels of the business.
The importance of a structured Business Intelligence Model
As cybersecurity programs grow more complex, organizations can no longer rely on static reports, manual reviews, or fragmented data to validate the effectiveness of their safeguards. Without structure, reporting becomes inconsistent, metrics become meaningless, and decisions are made without the context of real-world risk. A structured model like CRF-BIM ensures that cybersecurity validation is standardized, automated, and tailored to each stakeholder—from boardrooms to technical teams.
How the CRF Business Intelligence Model works
The CRF-BIM process starts by defining the safeguards that matter most, based on compliance needs, risk posture, and business priorities. These safeguards are then mapped to the tools and processes that implement them, aligned to specific vendors, and connected to data pipelines for validation. That data is centralized, normalized, and visualized through business intelligence tools—giving executives high-level summaries, business units operational insights, and security teams the technical metrics they need to act fast. The model ends with structured reporting, ensuring the right metrics reach the right audience at the right time. The result is a living, continuously improving cybersecurity program that can scale with evolving threats.
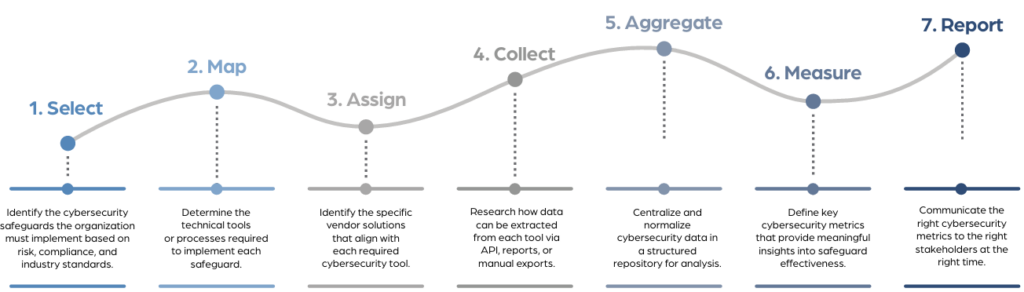
CRF-BIM enables automation across the full lifecycle of cybersecurity validation.
It bridges the gap between technical detail and executive decision-making.
Centralized data and real-time metrics reduce uncertainty and response time.
The model helps detect misconfigurations and safeguard gaps early.
It supports governance by aligning reporting to risk, not just compliance.
Frequently Asked Questions
The CRF-BIM is a seven-step process that helps organizations automate the validation and reporting of cybersecurity safeguards by structuring data collection, integration, and communication.
Any organization looking to improve how they validate, report, and govern cybersecurity safeguards—from SMBs to enterprises—can benefit from implementing CRF-BIM.
Start by identifying your organization’s required safeguards using a standardized catalog like CRF-Safeguards, then follow the seven-step model to align tools, collect data, and build out reporting.
