Governance & Risk Model
What Is the CRF Governance & Risk Model?
The CRF – Governance & Risk Model (CRF–GRM) is a practical framework for managing cybersecurity risk through a structured, business-aligned approach. At its core, the model helps organizations make smarter decisions about which safeguards to implement, how to manage risk consistently, and how to ensure that cybersecurity efforts support long-term business resilience.
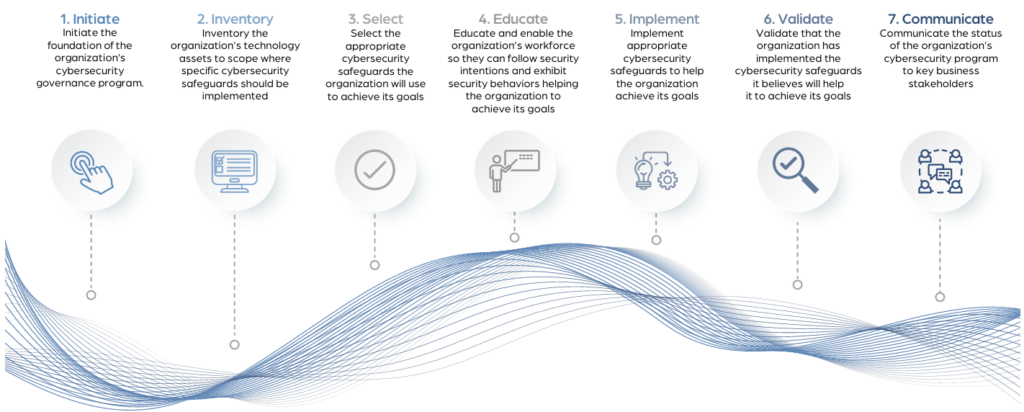
What sets the CRF–GRM apart is its prescriptive GRC Roadmap—a seven-step methodology that walks organizations through the full lifecycle of cybersecurity governance, risk management, and compliance. From establishing leadership commitment to validating controls and communicating outcomes, the roadmap provides a clear, repeatable process for building and improving a cybersecurity program that delivers measurable results.
Why You Need a Structured Governance and Risk Model
Cybersecurity is no longer just a technical challenge—it’s a business one. Without a structured approach, governance becomes fragmented, risks are inconsistently managed, and compliance efforts often fall short. The CRF–GRM provides a clear framework for organizing your cybersecurity program around strategic priorities, regulatory requirements, and operational needs. It ensures you’re not just checking boxes—but driving measurable outcomes.
What You’ll Get
The 2025 edition of the CRF–GRM introduces a prescriptive, seven-step GRC Roadmap—a practical methodology for implementing cybersecurity governance in any organization. From initiating leadership buy-in to communicating program outcomes, the roadmap walks you through each phase of building a resilient, business-aligned cybersecurity program. It demystifies governance, risk management, and compliance with a step-by-step process that removes guesswork and builds confidence.
Key Takeaways
- Aligns cybersecurity strategy with business goals
- Provides a step-by-step GRC Roadmap for implementation
- Clarifies roles, responsibilities, and governance structures
- Helps standardize risk management and safeguard selection
- Emphasizes transparency, validation, and communication
Who Is This For?
The CRF–GRM is essential for:
- Security leaders formalizing governance structures and reporting practices
- Risk and compliance teams managing safeguards and regulatory alignment
- Executives seeking to understand how cybersecurity supports business outcomes
- Organizations looking to mature their cybersecurity program beyond technical controls
Whether you’re a startup defining governance for the first time or a mature enterprise improving compliance workflows, this model gives you a repeatable process to work from.
What’s New in v2025?
- GRC Roadmap: A prescriptive, seven-step methodology for implementing cybersecurity governance
- Business-Centric Framing: Refined focus on how cybersecurity supports mission-critical systems and outcomes
- Greater Clarity: Simplified guidance for aligning safeguards with risk tolerance and compliance needs
- Enhanced Communication Framework: Guidance for regular, executive-level reporting on security posture and risk
Frequently Asked Questions
The Governance and Risk Model is a comprehensive framework designed to guide organizations through the process of identifying, assessing, and mitigating cybersecurity risks. It emphasizes the importance of aligning cybersecurity initiatives with business objectives, ensuring a proactive approach to digital threats, and fostering a culture of continuous improvement.
In today's digital landscape, cyber threats are evolving rapidly, posing significant risks to organizations of all sizes. The Governance and Risk Model provides a structured approach to cybersecurity, helping organizations not only protect their digital assets but also ensure that their cybersecurity efforts support overall business growth and success. It's crucial for maintaining compliance, building stakeholder trust, and ensuring business continuity.
The model starts with program initiation, defining the scope, objectives, and governance structure of your cybersecurity efforts. It then moves through strategic safeguard selection, workforce education, asset inventory and prioritization, and the implementation and validation of cybersecurity measures. The cycle of continuous improvement ensures that your cybersecurity posture evolves in line with new threats and organizational changes.
Successful implementation of the model requires involvement across the organization. This includes senior leadership to provide strategic direction and resources, IT and cybersecurity professionals to manage technical aspects, and employees at all levels to adhere to cybersecurity policies and procedures. Additionally, a dedicated Cybersecurity Steering Committee can oversee and guide the program's implementation.
Begin by downloading the free PDF version of the Governance and Risk Model to understand its framework and principles. Next, establish a Cybersecurity Steering Committee to lead the initiative, and develop a cybersecurity program charter that outlines your strategy, objectives, and governance structure. From there, follow the model's steps to assess risks, select and implement safeguards, educate your workforce, and continuously monitor and improve your cybersecurity posture.